Fishing, Phishing and Network Security: It's all connected
4.8 (760) · $ 29.00 · In stock


Phishing or Fishing for Information: The Dangers of the IoT - i3 Information Integration Inc.

What Is Phishing? Examples and Phishing Quiz - Cisco

Why phishing is still successful — and is AI to blame? - SDxCentral
What is clone phishing, and how can you avoid it?

What is phishing? + How to spot and avoid it - Norton

What Is a Phishing Email Attack? Definition, Identification, and Prevention Best Practices - Spiceworks

What Is Phishing? Understanding Cyber Attacks
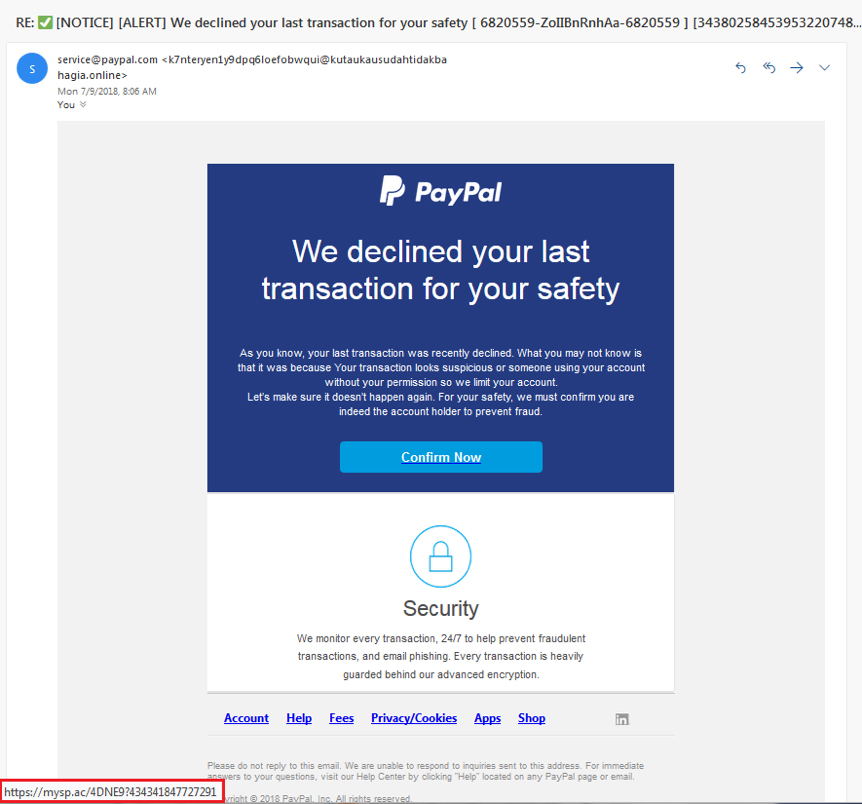
What is phishing? Protect yourself on the internet against attacks

New Generation of Phishing Hides Behind Trusted Services

There's Plenty of Phish in the Sea: How Organizations Can Avoid Getting Caught - Spiceworks

What is phishing? Examples, types, and techniques

Blog, RK Black, Inc.







