Phishing Hacker Technique, Vectors
4.8 (368) · $ 6.99 · In stock


Browser in a browser': Phishing technique simulates pop-ups to exploit users
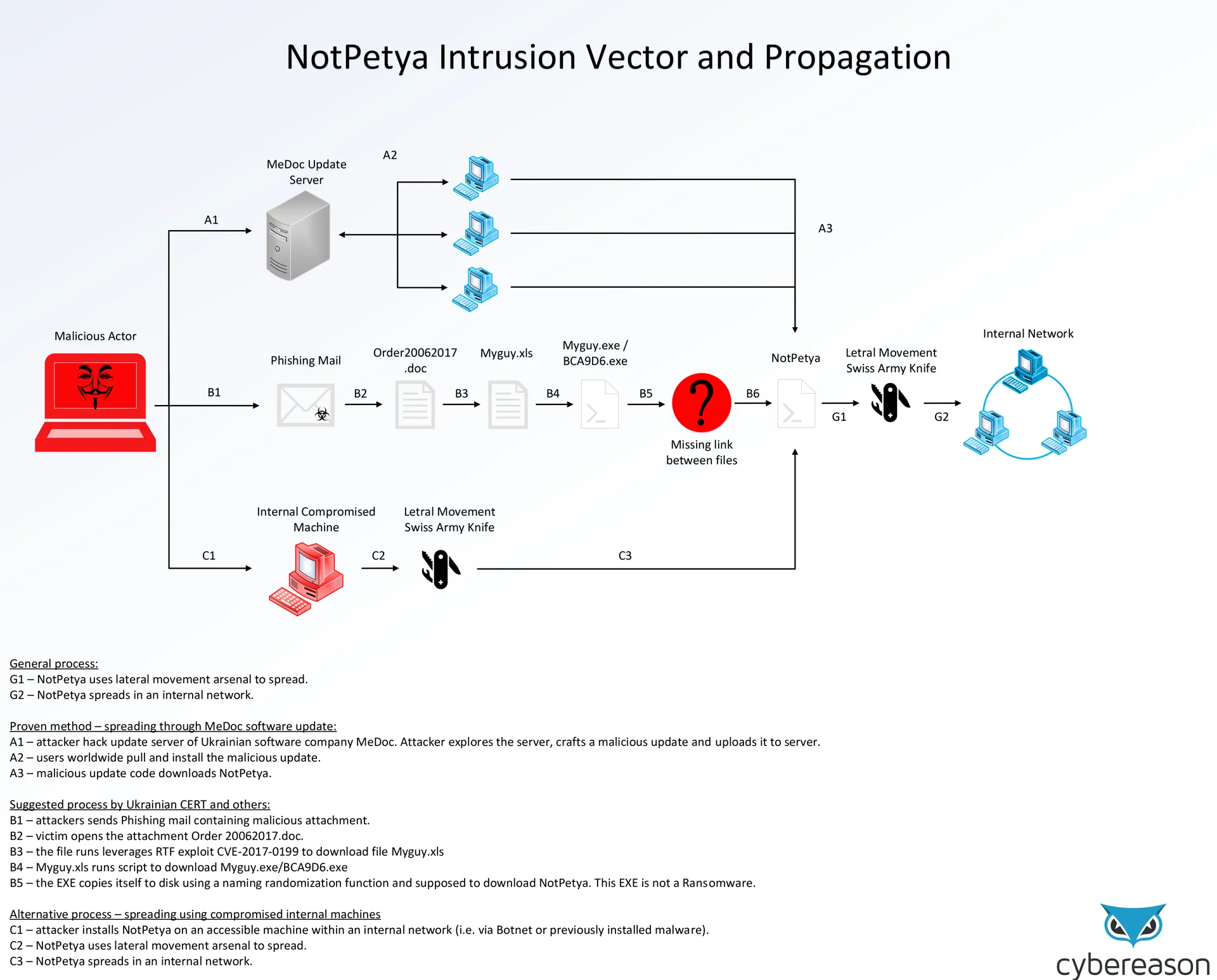
NotPetya intrusion vectors and propagation

Phishing technique used to steal digital data Vector Image

Phishing technique for acquiring unauthorized Vector Image
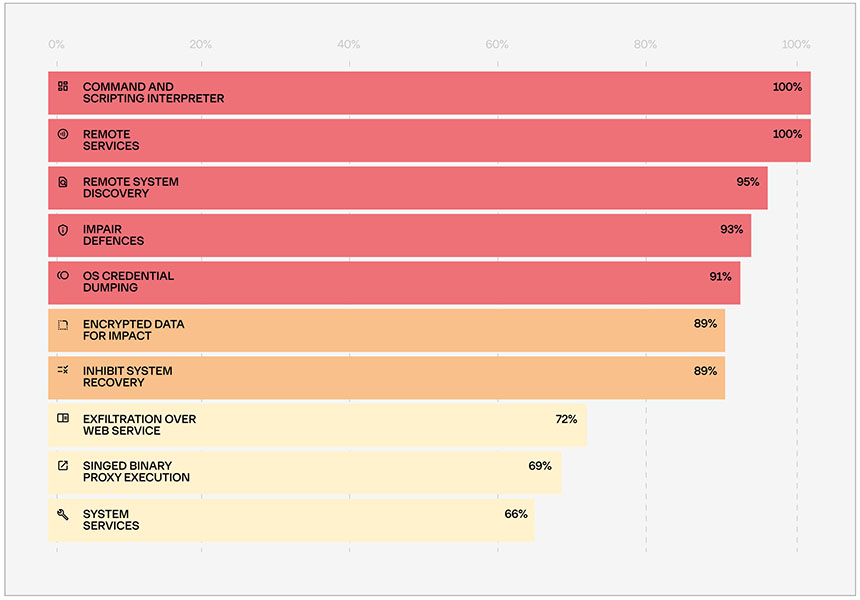
Ransomware Attack Vectors: RDP and Phishing Still Dominate

Phishing technique used for scamming and fraud Vector Image

Common Phishing Attack Vectors

Hacking Techniques, Breach Effects and Prevention Tips

5 Phishing Techniques Organizations in the MENA Region Should Be Aware of - Kratikal Blogs

Cyber Security Attack Vectors - Common Cyber Threat Vectors

The Latest Phishing Statistics (updated April 2024)
Mobile Security - Attack Vectors
Phishing Funnel Model Download Scientific Diagram

What is an Attack Vector? 17 Common Examples in 2024
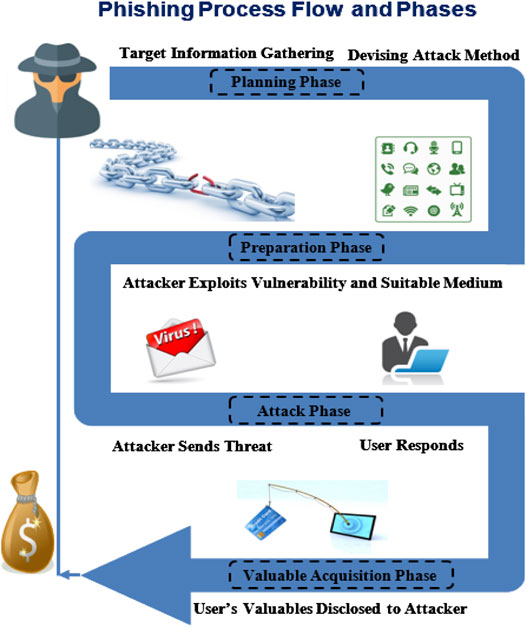
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy







